Businesses want to stay competitive in the ever-changing digital landscape. But as the world grapples with complex cyberattacks and data breaches, how will they ensure that data is sufficiently secured? Poor IT security can be detrimental to business growth and can inevitably lead to data loss and non-compliance penalties. In fact, according to IBM's Cost of a Data Breach report, the average cost of a data breach in 2022 is $4.35 million.
To protect their assets and data, organizations must continually test and improve their infrastructure security, and a red team assessment should be on their to-do list. NIST defines a red team as a group of people authorized and organized to emulate a potential adversary's attack or exploitation capabilities against an enterprise's security posture. By giving the blue team (the defenders) the experience of a real-life attack, the red team aims to demonstrate the impact of exploitable vulnerabilities to improve enterprise cybersecurity. As the years go by, red teams will become an integral part of security operations centers (SOCs).
Let's see how a red team differs from pen testing, and how they play their game.
Pen testing and red teaming are both attack simulations performed in-house or via a third party. However, they are not synonymous and not to be confused with each other. Pen testing is done to find bugs and vulnerabilities in a system or application, and report them to the management. In comparison, a red team's objective is to try all means to quietly infiltrate the network to the furthest extent and test the organization's defenses against it. This might also entail the use of social engineering techniques to target vulnerable human identities in a network.
While pen tests are usually scheduled and announced with the blue team's knowledge, red teams operate covertly, with only senior management knowing that such a stealth operation is underway. The red team normally reports to the CISO or the top management and has autonomous authority.
The main differences between red teaming and pen testing are detailed in the table below.
| Pen testing | Red teaming |
|
|
An example of pen testing includes checking a newly developed website for bugs and vulnerabilities using Burp Suite toolkits or vulnerability scanners. Red team exercises may consist of targeted spear phishing and sometimes calling sysadmins and asking for password resets while claiming to be an employee.
In a nutshell, pen testing is like lab-based testing that checks vulnerabilities in network systems and applications. A red team goes beyond pen testing by targeting people, processes, and network assets to infiltrate the organization.
Sometimes red team members are engaged in pen testing as a part of their operation or as required by the organization. Choosing between pen testing or red team operations largely depends on the organization's requirements and security maturity. Businesses with an established SOC process will go for a red team assessment. The more defense mechanisms an organization has put in place, the more it can test and learn through a red team exercise. Red teaming is more expensive than pen testing due to its depth of evaluation and prolonged period.
Here are the four stages involved in pen testing:
Pen testing is repeated after the fixes are made, continuing the cycle. If the objective is to pen test a web server, some recommendations could be tweaks to firewall policies before rerunning the test.
A red team assessment can happen over a few months, closely resonating a real-life attack. Red team operators use this extended time to start from scratch, gather information, research, target vulnerable entry points, and slowly perform lateral movement to reach their objective.
Let's suppose that the objective of a red team exercise is to demonstrate the security posture of the organization. To accomplish this, red team operators may attempt to access sensitive data from the client's network or deploy dummy malware that displays a ransom message by exploiting vulnerabilities and evading defenses.
Here are the stages of how a red team plans its operations:
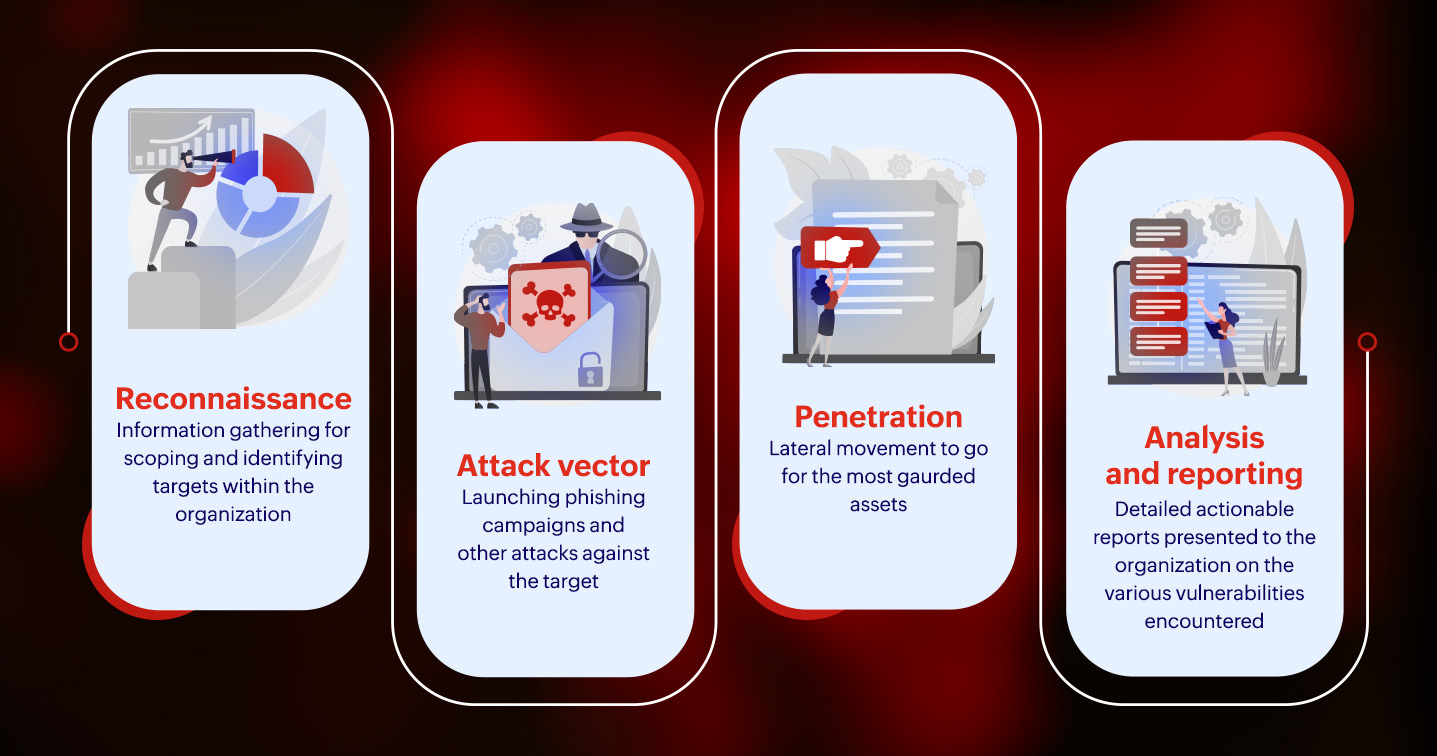
Reconnaissance: The information-gathering stage lays the foundation for the whole operation during which the red team learns about the external network perimeter of the target organization to identify potential opportunities.
This is done using open-source intelligence tools to get a public view of the network. Shodan, for instance, is a search engine for publicly available IP addresses of any devices connected to the internet, such as servers, routers, IoT devices, etc. By narrowing down the search to a particular location and company, one can find devices, ports, and software versions.
With the enumerated information, the red team now targets vulnerable users for phishing or devices with outdated or unpatched software. The identified targets are now analyzed for any misconfigurations.
Attack vector or initial access: If the objective is to deploy dummy ransomware, the red team engages in spear-phishing campaigns targeting potential employees. Such social engineering campaigns are creative and could be in multiple stages. One example is sending emails posing as a customer, establishing contact, and asking the target to download an attached file named quote.
Penetration: After initial access, the red team will test how much further they can go. By laterally moving across the network, the red team will try to escalate privileges gradually and infiltrate the most guarded assets or data in the organization while staying undetected. This extended stay examines the different defense measures and response mechanisms in place and how they function.
Analysis and reporting: The red team completes the operation by submitting a thorough report on the client's network that lists all the vulnerabilities they encountered. The red team offers actionable insights for the organization to understand and refine its security posture.
Here's an interesting insight from SangeethaRajesh S, a Red team member at Zoho Corporation Pvt. Ltd.

You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.