Malware does not dress up like a burglar and knock on your door. It impersonates your friend or a known face to gain entry. Sometimes it's wrapped in a beautiful e-commerce gift package that you might open excitedly. Or it can break in using lost or stolen keys to your door. If nothing else works, you still have open windows it can sneak through. The ways are numerous. Hold on as I explain what this looks like in an enterprise network.
For starters, malware is any malicious software designed to damage and destroy your IT. Malware includes viruses, worms, Trojans, adware, ransomware, and spyware. Knowing how threat actors try to sneak these malicious pieces of code onto your computers is crucial to your cyberdefense strategy.
Here are five ways malware can enter your network.
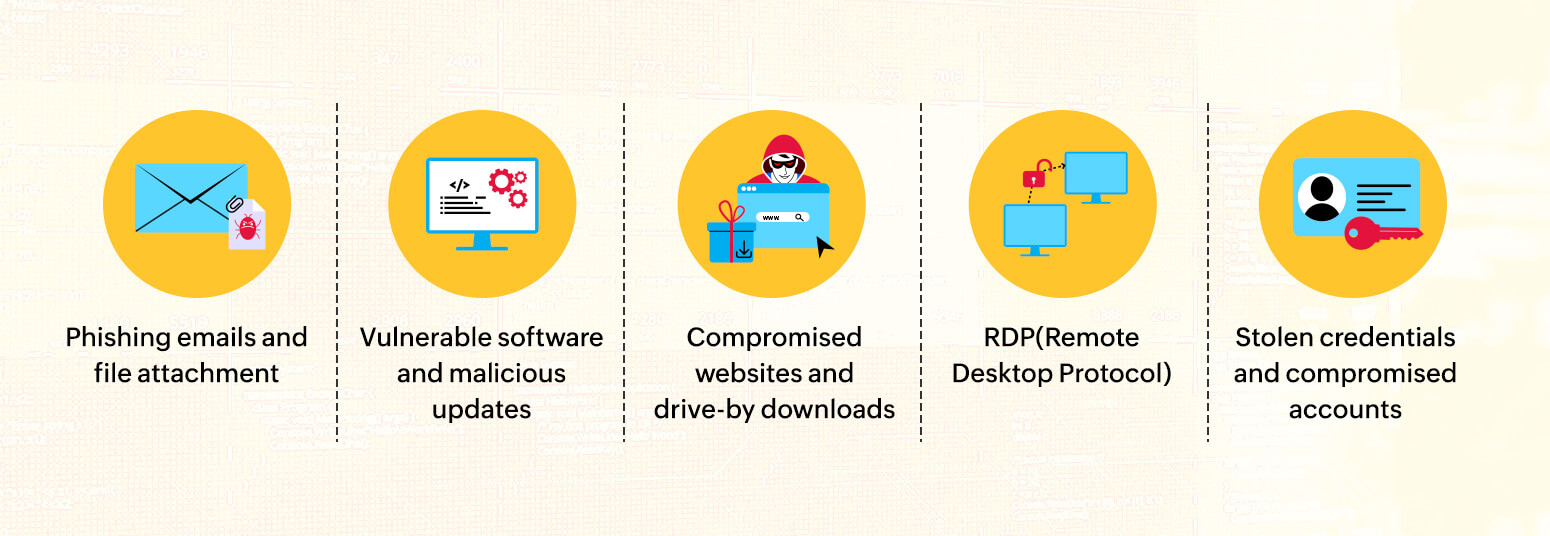
Phishing emails are the most common entry point for attackers. Such emails usually come in the guise of a trusted organization or a customer sending a personal message and use social engineering techniques. These emails ask you to either download a file attachment or click a URL that ultimately downloads malware onto your computer.
Before downloading attachments or clicking links, pay close attention to the email structure and content and confirm the sender's domain. Using your SIEM to set inbound and outbound rules in your firewall to block malicious URL requests is one proactive way to thwart a possible malware deployment.
Unwary users visiting compromised websites run a huge risk of downloading malware. Attackers can take control of the website's back end and sometimes set up spoofed or cloned websites of established brands.
Adware redirecting users to malicious URLs is a highly prevalent method of deploying malware. Examples of these ads include clickbait that claims to offer free coupons and gifts. Drive-by download attacks deliver malware to your computer without your consent when you click a link or navigate through a website. Ad blockers and browser security tools can help you avoid adware and malicious downloads.
We install various third-party software on our computers. Threat actors can exploit any vulnerability in the software to inject malware into update packages, which are deployed when the user downloads or updates the software. Anti-malware, EDR, and SIEM solutions can aid in the detection of suspicious downloads and malware deployments.
RDP is a Windows service widely used by admins to connect remotely to servers or other computers. RDP transmits the display of the remote device to the admin, effectively giving them complete control so they can access files and troubleshoot issues.
Threat actors scan for exposed RDP ports on the internet and try to get in using stolen credentials or brute-force techniques. Once in, it is easy to disable defenses in the end user's system and drop the malware payload.
RDP-based attacks can be mitigated by ensuring all open RDP sessions are ended and disconnected. VPNs can be used to securely connect to the company network without exposing open devices to the internet. Using MFA is also an effective way to reduce remote logins by threat actors.
Using the same password for personal and work accounts puts the enterprise at risk. If a user's personal account is compromised due to a weak password, threat actors can use this to break into the user's work accounts and deliver the payload. Stolen credentials, too, are a significant facilitator of malware attacks. Compromised cloud storage accounts can also be used to inject malware into files that are deployed on a device when downloaded.
Single sign-on with MFA is a great measure to mitigate weak passwords and suspicious logins. Using a CASB to monitor what moves into and out of the cloud helps you detect malicious uploads and downloads.
When it comes to cyberattacks, the road is full of surprises. The five methods discussed above are among the many ways attackers try to enter your network. However, many such methods employ common social engineering techniques to bait the end users. It is crucial to stay updated on cybersecurity best practices in order to avoid becoming a victim.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.